Linux Kidnapping Case
To date, I have not added any material on Linux forensics on to this Substack yet. I think that now is the best time to do that. This post is my response to the Belkasoft CTF “Kidnapping case (Belka CTF 4). Please note that there are already answers published for this CTF, so I will not copy them exactly. I will, instead, use them for help if I need assistance.
Hello everyone. It seems that 2026 is off to a great start so far. I’ve got one Mac post out and I’m ready to start posting some Linux forensics, as I haven’t done that yet. Lately, on my free time, I’ve been looking into Mac and Linux forensics and I wanted to share some more info on Linux forensics. For lack of creativity at the moment, I decided to write on another CTF: the Belkasoft CTF named “Kidnapping Case.” Since this CTF is done, I will be rehashing the CTF in my own words. I may or may not heavily use the stuff from the CTF as I write this.
Let’s get into the challenges. There are ten challenges, so this will be shorter than the last one.
Users
List all users of the computer.
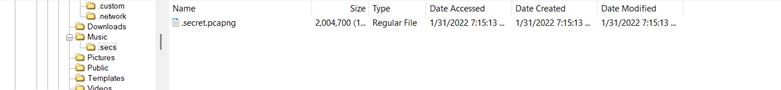
This question was easy, very easy. It takes a couple of seconds to do. Once you get it into Belsasoft (or in my case FTK Imager) you will find a total of two folders within /home/ that indicate profiles. They are named ivan and stanley.
Answer: ivan, stanley
Special Web Site
What web application was used by the boy to earn his pocket money?
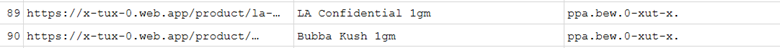
Each of the user folders have evidence of Mozilla Firefox being used. This evidence comes from the .mozilla folder that exists in the /home/ folder. It specifically comes from a file called places.sqlite that comes from the path /home/ivan\/.mozilla/firefox/yyxsdegu.default-release/.
You can open this with DBBrowser for SQLite and you will see some entries within the moz_places table that shows a link to some odd site. It goes by the name of a site
https://x-tux-0.web.app
that is seemingly this site.
Answer:
https://x-tux-0.web.app
Wallet
Which BTC wallet did the boy use to sell drugs?
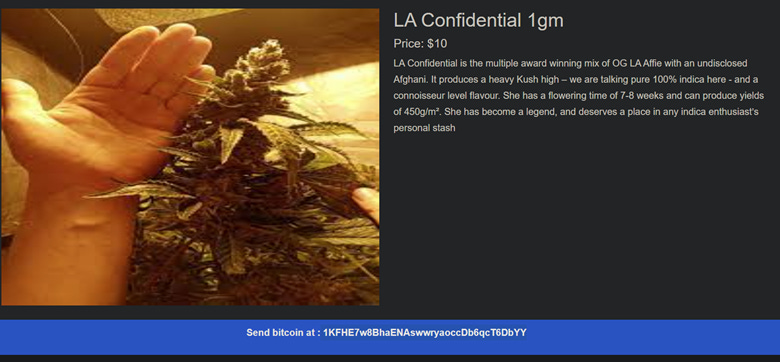
This evidence is a bit confusing to find. I originally thought that the wallet was going to be in a picture. I found nothing. After switching up my method, I went to one of the websites present in the second question and found this:
Answer: 1KFHE7w8BhaENAswwryaoccDb6qcT6DbYY
Passme
On which date does the kid’s database show the most sales for “Acapulco Gold”?
Flag Format: YYYY-MM-DD
When I was first parsing this clue, I thought this evidence was in the web history artifacts. I checked the web history in both /.mozilla/ folders. This search for any evidence of numbers came out empty.
After failing with the /.mozilla/ folders, I noticed that the second profile had a folder named /.db/ which I thought may hold some evidence of “Acapulco Gold”. I expected it to also have something protected with a password or a document with passwords to accounts on it. I was surprised and disappointed that the first option was what they went with,
The folder had many subfolders and only two of which had any contents. There was a Dec and a Jan folder that had contents. Both folders contained locked zips: one named Monthly_DB.zip (Dec) and mycon.zip (Jan). I tried both of them. After a long series of tries, I discovered that the password to the mycon.zip was 1257. The other is unknown. It was supposed to be able to be cracked with something, according to the answer, but I could not crack it with John the Ripper because the hashes for the password were not right. I got as far as finding that out before I decided that I was taking too much time and quit.
Cryptlet
What was the other BTC wallet of the victim, which he used to hide his “under the counter” sales from his superior?
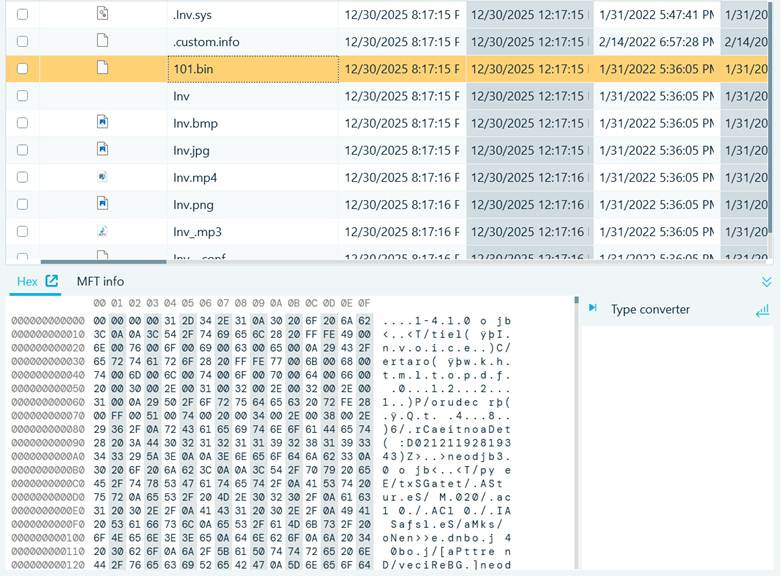
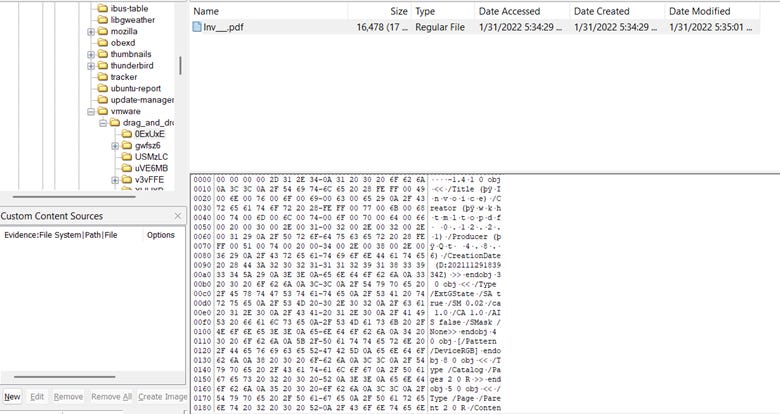
For this question, I had another instance of being partially complete. This is another one where I had trouble. I looked around a bit and noticed that there was a folder named /.custom/ in /home/ivan/downloads/ that had many PDFs in it. Each file was a PDF, but some of them were corrupted like the example below. I specifically looked at the one highlighted in the image below.
I exported it and changed the first few bytes to show the bytes of a PDF, as shown in the image below. It was unfortunately unsuccessful at revealing something that was PDF-like.
I could not find this. I am mad that I couldn’t decode that PDF that I found.
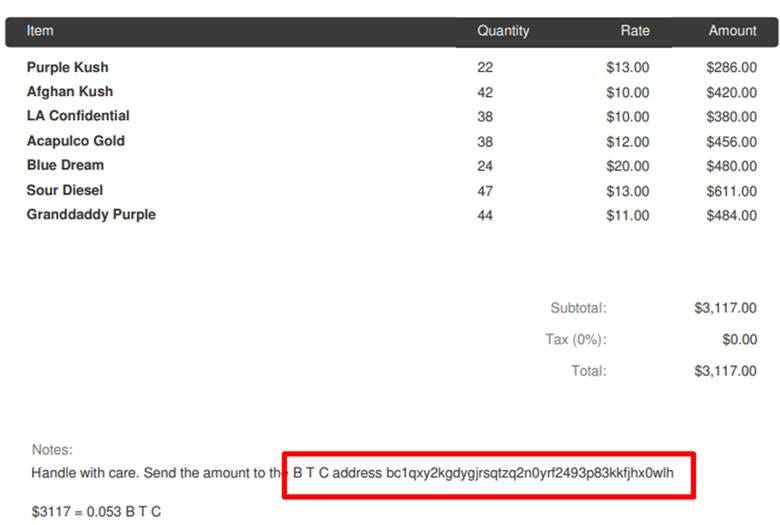
During the looking for the answer for Notipass, I managed to find the answer for myself in the file inv_.pdf within the folder /home/stanley/.cache/vmware/drag_and_drop/oExUxE/
Answer: bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh
Notipass
What is the password to the boy’s notes?
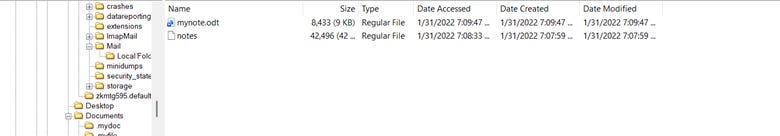
For this challenge, I looked for notes and I found two odt files. One odt file was actually an odt file and the other was labelled as a plain file. I found these files in /home/Stanley/Documents/.mynote/. This material is shown in the image below.
The plain file is the file that we want. After renaming it and opening it, it asks us for a password. This is also where I stopped because I couldn’t figure out how to decode the next part from the hints.
After looking at the answer, I found that I had to go to a file called NOTHING_IMPORTANT_INFO.pdf that lives in …
After this, I had no idea how to get the necessary information out of the PDF, so I just moved on. I will add the answer and you can comment on how to get the rest further
Answer: !mp0rt4nTNot3
Specudio
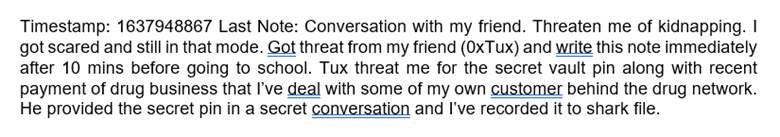
What is the “secret pin” mentioned in the notes?
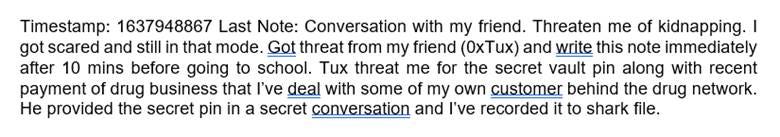
For this one, I didn’t understand at first, but after reading through the notes document, I was even more confused. I didn’t know what to look for since it was all ML notes and things from other documents. I kept reading for anything interesting. Something interesting came at the end.
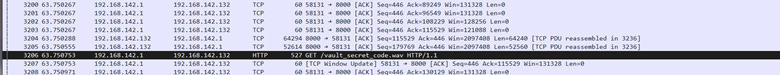
The writer speaks of a threat and a “vault pin”. This vault pin comes from a “shark file”. This could be one of two things: another hint or a red herring. I spent more time looking for answers. Specifically looking for network traffic files, I came up with this:
I exported this file and analyzed it.
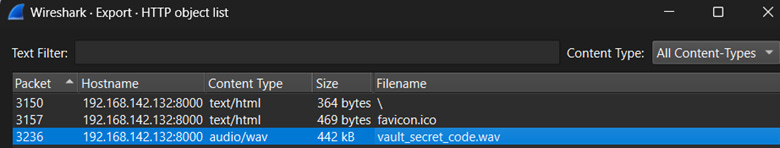
One of the most important things I saw in this “shark file” was the transfer of an audio file called secret_code.wav. I extracted that file from the capture and did other things with it, which I will describe next.
This was one of two files that made any sense in this capture.
The audio contained in the file sounds like a bird chirping and a dog barking all rolled together; there’s nothing interesting in the audio. This led me to think about what I’ve used before to do CTF challenges with audio.
I installed Audacity and put it through the spectrum analyzer. It turned out that there was in fact some spectrum shenanigans.
Answer: flag{1257}
Ultimatum
When did the boy receive a threat? (Format: Epoch Time)
The answer is here:
1636948867 is the time in epoch time when this note was taken. Doing the math of ten minutes before, we need to subtract 600 seconds for our answer. This leaves us with an answer of 1637948257.
Answer: 1637948257
Whois
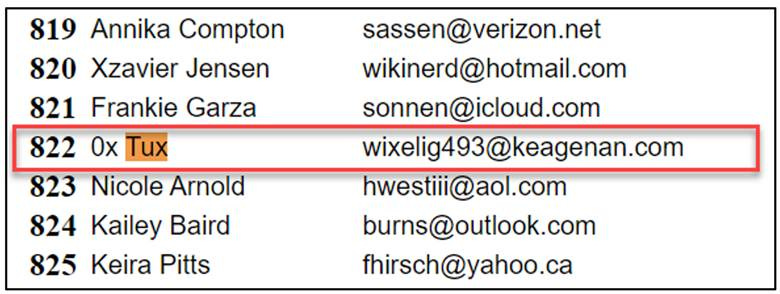
Who is the kidnapper?
This is simple. I remembered the password from a couple of questions ago. I just had to find where to put that. I ended up finding another locked zip folder at /home/stanley/.cache/vmware/drag_and_drop/v3vFFE/mycon.zip. I opened this zip folder with the password 1257 and found the following information in a file called sheet1.html.
Answer: 0xTux, wixelig493@keagenan.com
Conclusion
I think that this CTF would have been fun if I were doing it when it was live. I say this because, as you saw from some of the clues, there was a great amount of variety in the things that they challenged players to do. Also, I would have had a great deal of challenge getting the first locked zip unlocked. This would have made the event even more worth talking about.
I firmly believe that all of these events have something to teach, even if we are doing them multiple years later. My biggest takeaway from doing this is that I forgot a lot about hacking and need to do a bit of relearning. This was evidenced by that first locked folder question. I remembered there being a site online that allows its users to upload and crack locked folders but was unable to find it. I struggled to get John the Ripper working and gave up after a few hours of trying to brute-force crack the folder. I just need to be more patient and learn John the Ripper next time.
For the other challenges, there were some good ones and some easy ones. I think all of the rest were good. I especially liked the one called “Specudio” since it required multiple steps. I made quicker work of that one than expected because I took a look at that Wireshark file earlier on, after finding it while looking for the password for the locked zip. I opened it, half expecting to find a packet with a password. I immediately knew it was for something else when I saw the downloaded audio file.
I really disliked the Cryptlet and Passme questions since they were both tedious in their own way. Passme took too long and Cryptlet almost did the same thing: I was about to call it a fail until I found it in the /home/ivan/.virtualbox/ folder. Good thing that happened!
In all, this was a good glance into Linux forensics. Hopefully you enjoyed this and found something useful. If you did, make sure that you let me know. Until next time, this has been Matt talking about Linux Forensics. Matt OUT!

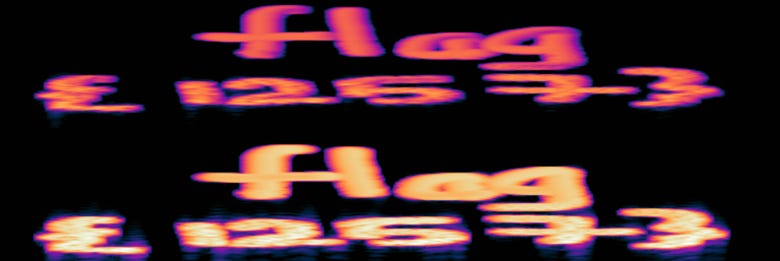
Very interesting, I've always wanted to try a CTF, and never thought to look for old ones to brush up on techniques first.